
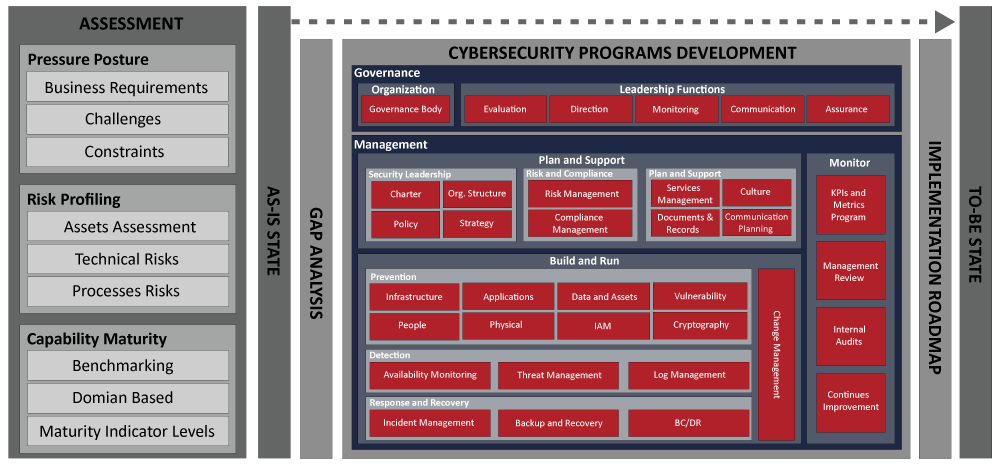
Cyber Security Program Development
We all have challenges and constrains
Managing widely spread information either of your customers or of partners becomes more difficult and challenging, and this sometimes leads to open new doors for adversaries. Changes on technologies, business requirements, supply chain channels, compliance and regulations, and the constant evolving of security threats all make the goal of maintain secure environment harder and harder. Having a customized, personalized, comprehensive, and integrated set of programs enable you to have best investment choices with unified direction to make your business success at its core.
To understand the importance of having such programs, imagine that each unit at your organization had responsibility for the entire security of its own IT systems at your datacenter. Now, suppose each unit had its own separate strategy, policies, standards, procedures and approach to maintaining continuous protection and safety of the valuable informational assets inside individual systems. Moreover, assume each system had interconnecting tunnels, which may or may not have protection but had direct access to each other system bypassing the protection that unit was providing.
The question is how each unit would be satisfied when they confident on the security of their particular system but they could not ensure the degree of security that other units was providing. Individual unit cannot achieve complete security.
Build it to fit your business
Building your cybersecurity programs on bases of your desired Return on Security Investment (ROSI) factor will not be sufficient to compact adversaries. Our extensive experience on threat landscape advances and adversaries’ Tactics, Techniques, and Procedures (TTPs) will add another major factor to the formula; Adversary’s Return on Investment (AROI) – defensive vs. offensive mindsets. Applying this approach of thinking will help you to build a risk-based cybersecurity program defined with controls suitable to your business context and driven by industry best practices.
Our Promise
Cybersecurity is not one-size-fits-all; every client requires a unique blueprint. TechArch’s harmonized mixture of experience in cybersecurity, management consultancy, and R&D fields enable us to develop the best-fit blueprint for your business requirements.
A careful and planned methodology ensures that security concerns receive prompt and informed attention and are incorporated throughout planning, execution, and delivery. Such methodology puts you in a strong position to achieve effective risk reduction while meeting budget, schedule, and business objectives. We designed our methodology for developing cybersecurity programs to be phase-based (i.e. not big bang), driven by your business context, and domain-focused.
Get in touch
Send us your requirements using the below button and we will get back to you soon